Key Takeaway
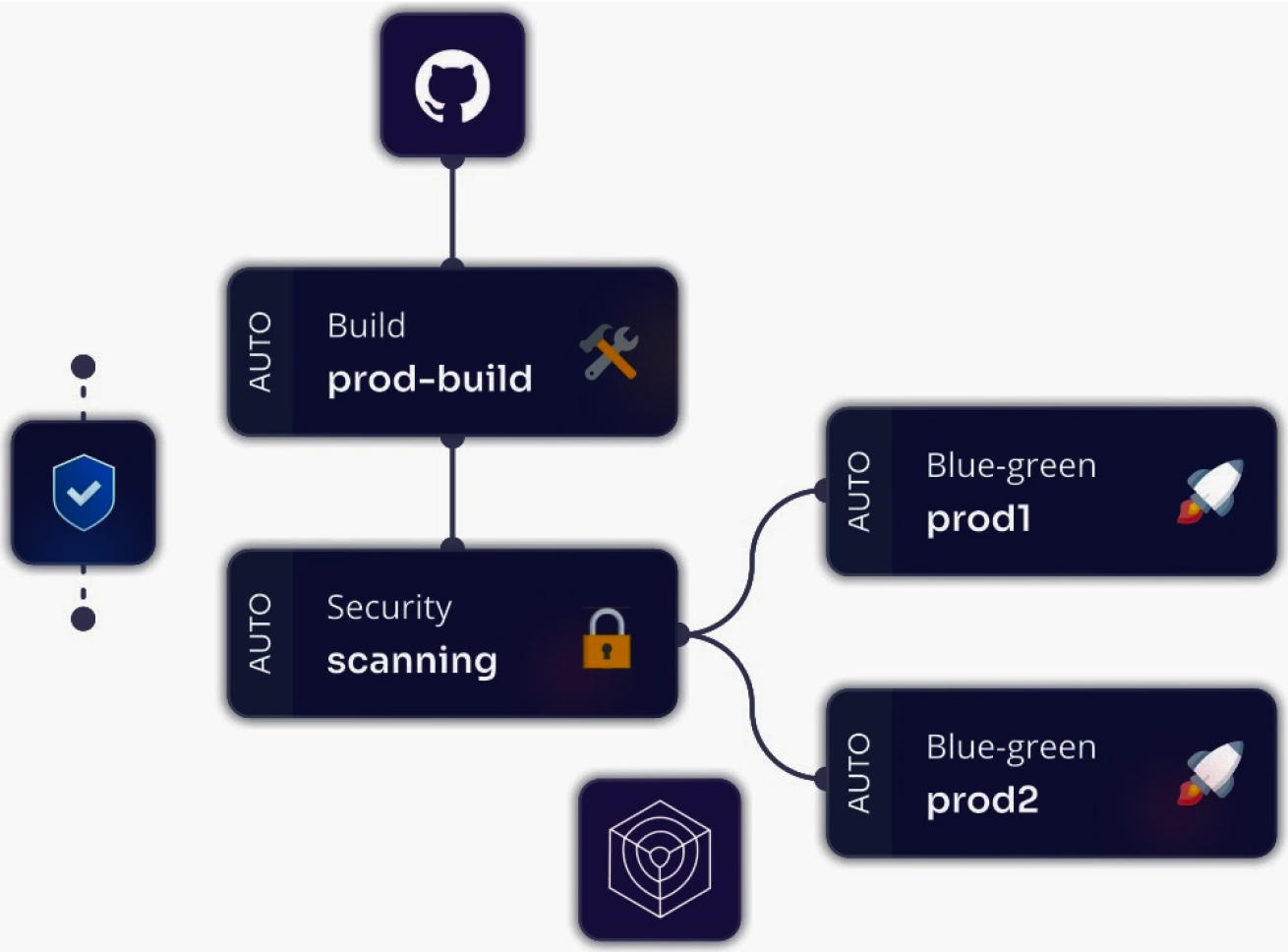
- Early Security: Integrates security from the start to catch vulnerabilities before production.
- Continuous Protection: Automates security checks in the CI/CD pipeline for ongoing threat defense.
- Simplified Compliance: Automates compliance checks to meet regulations effortlessly.
Unified DevSecOps
Integrates security practices into the DevOps process.
Focuses on automation, monitoring and early identification of vulnerabilities.
Aligns development, operations, and security teams for faster, secure software delivery.
Enhanced Security and Faster Time-to-Market
-
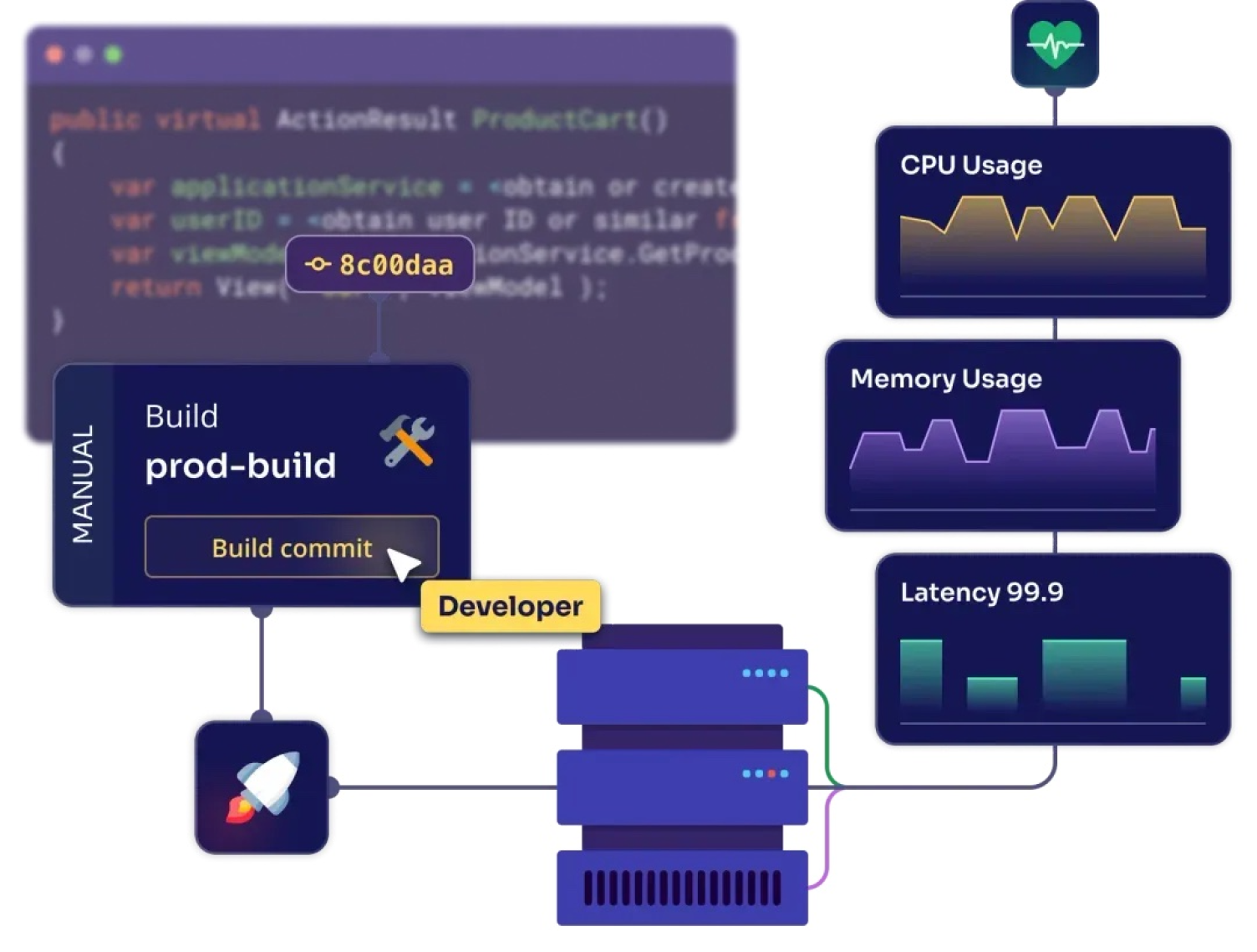
Identify and mitigate security risks early in the development process, reducing vulnerabilities in production.
-
Automate security testing and compliance checks to maintain the speed of development and deployment.
Cost Efficiency, Collaboration and Culture
-
Reduce the cost of fixing security issues by addressing them during development rather than after deployment.
-
Foster a culture of shared responsibility for security across development, security, and operations teams.
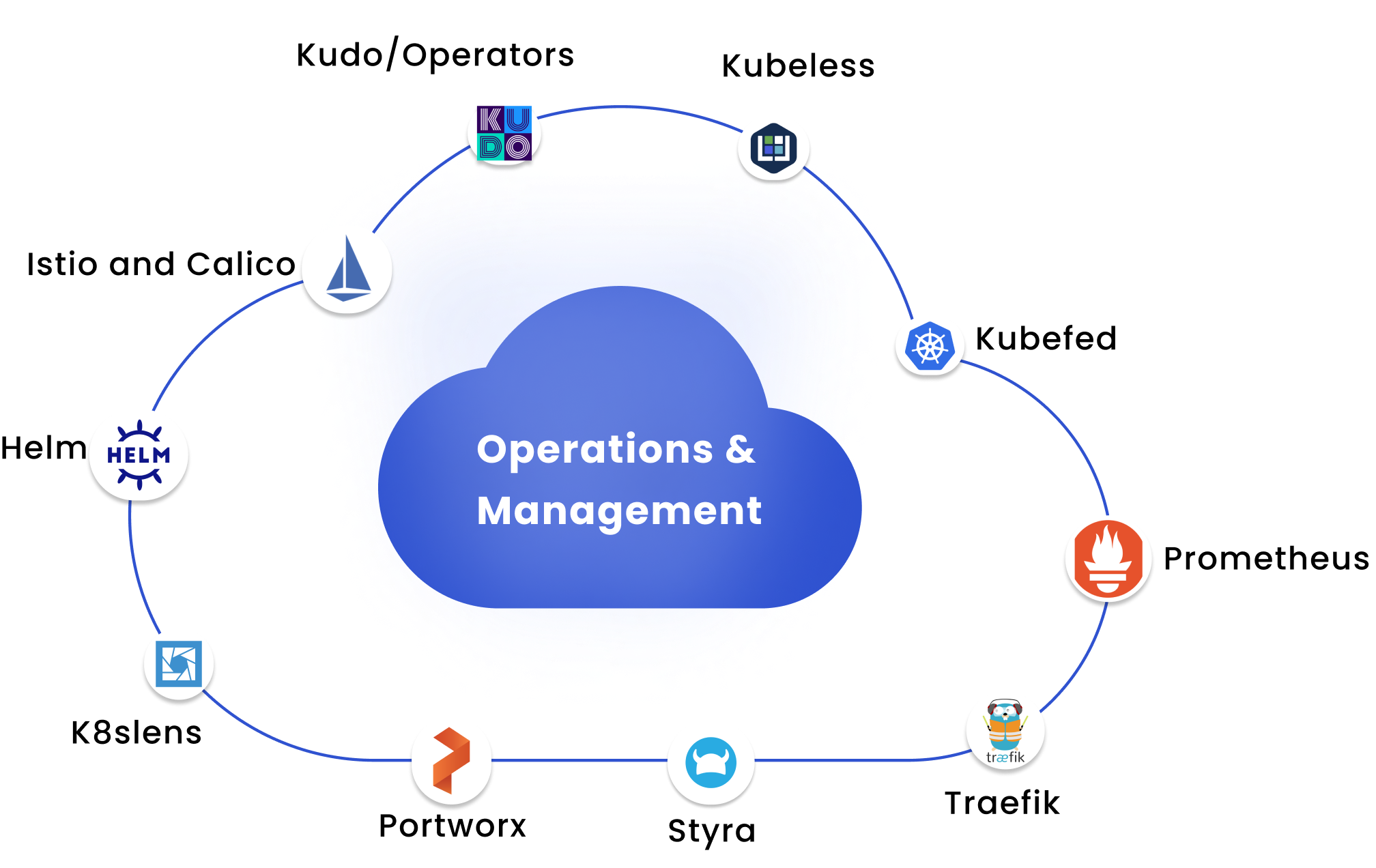
Integrated Security Tools
-
Static Application Security Testing (SAST): Automatically analyze source code for vulnerabilities during development.
-
Dynamic Application Security Testing (DAST): Simulate attacks on running applications to identify potential weaknesses.
-
Software Composition Analysis (SCA): Detect vulnerabilities in open-source components and third-party libraries.
 Fast, Intelligent Automation Co-Pilot for Seamless QA — Explore Now!
Fast, Intelligent Automation Co-Pilot for Seamless QA — Explore Now!
 Fast, Intelligent Automation Co-Pilot for Seamless QA — Explore Now!
Fast, Intelligent Automation Co-Pilot for Seamless QA — Explore Now!